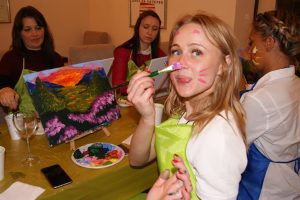Speaking Time в Шымкенте известен своим индивидуальным подходом к обучению и использованием инновационных методик.
Выбор подходящего напольного покрытия для дома, где есть домашние животные, представляет собой сложную задачу.
Заказать ткань для пошива одежды – это первый и один из самых важных шагов
Индивидуальные металлические значки являются превосходным способом выделиться из толпы и придать вашему мероприятию, бренду
Переработка лома алюминия начинается с его сбора, сортировки по типам и очистки от загрязнений.
В этой статье мы рассмотрим, какие меры необходимо предпринять для эффективной охраны вашего товарного
Выбор петличного микрофона – это решение, которое может кардинально изменить качество аудиодорожки ваших видеоматериалов.
Эти арт-встречи привлекают людей, которые не обязательно имеют опыт в живописи, но желают попробовать
Замена дверных замков - эффективный и необходимый шаг для обеспечения безопасности вашего дома или
Преобразование женского пуховика с течением времени отражает изменения в модных тенденциях и технологиях производства.
Использование виниловых надписей позволяет не только выразить личные предпочтения, но и создать определенное настроение
В современном цифровом мире Телеграм выступает не только как платформа для общения, но и
Поддержание водно-солевого баланса в организме человека является одним из основополагающих аспектов поддержания здоровья и
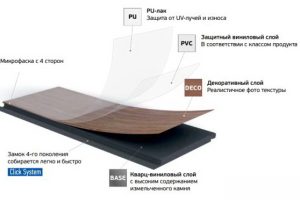
SPC ламинат Фарго - это инновационный тип напольного покрытия, который сочетает в себе лучшие
Футбол имеет богатую историю, которая начинается еще в средние века. Современный вид игры начал
Танец – это искусство, которое не знает границ. Он может быть выражением чувств, способом
Военно-полевая кухня – это мобильное устройство, предназначенное для приготовления пищи в условиях, где нет
Обучение в J-center Studio ведется в соответствии с высокими стандартами, что гарантирует качественную подготовку
Рыбалка - это не только увлекательное хобби, но и искусство, требующее правильного подхода и
Давайте продолжать исследовать кулинарное наследие мира и радовать себя и близких уникальными блюдами из
Сервисы, такие как аренда аттракционов, предлагают удобный и гибкий способ привнести атмосферу праздника в
На первый взгляд квадроциклы и квадрициклы могут показаться очень похожими, однако между этими двумя
Дистанционное образование, ставшее особенно актуальным в последнее десятилетие, революционизировало подход к обучению и доступу
Букет невесты «Алмазная Россыпь» – это не просто аксессуар, а важный атрибут, подчеркивающий красоту
Современные рюкзаки изготавливаются из высококачественных материалов, обеспечивающих долговечность и надежность.
Обменники валюты играют ключевую роль в международных путешествиях и глобальной экономике, обеспечивая удобный доступ
Детская стоматология отличается от взрослой особой акцентированностью на комфорт и психологический аспект взаимодействия с
Толстовки с принтами на заказ стали важным элементом современной моды, предоставляя возможность выразить свою
IT-курсы предлагают актуальные знания и практические навыки, которые необходимы для успешной карьеры в этой
Перевозка инвалидов – это важная часть обеспечения их мобильности и независимости. Это требует особого